Tor, short for “The Onion Router,” allows users to traverse the internet anonymously, shielding their online activities from prying eyes, be it governments, corporations, or malicious hackers.
Yet, with great power comes great responsibility. Using Tor effectively and safely requires understanding its mechanisms and a firm grasp of the precautions and best practices to ensure your online presence remains private and secure.
This guide will provide you with step-by-step instructions, expert tips, and invaluable tricks to help you harness its power while safeguarding your digital identity.
So, whether you’re new to Tor or seeking to enhance your expertise, join us as we delve into the depths of the Tor network, ensuring that you navigate its labyrinthine layers with confidence, security, and the utmost respect for privacy.
Understanding Tor Basics
What is Tor?
At its core, Tor is a network of servers, often called nodes, that relay your internet traffic through encrypted connections. The name “Onion Router” is derived from the layers of encryption used, akin to peeling an onion. Each node in the Tor network only knows about the node before and after it, obscuring the origin and destination of your data.
How Tor Works
Tor bounces your data through a randomized series of nodes, making it extremely difficult to trace back to your original IP address. This process involves three key types of nodes:
- Entry Nodes: These are the points at which you enter the Tor network. They encrypt your data and pass it to the next node.
- Middle Nodes: These nodes further encrypt and pass your data along the chain.
- Exit Nodes: The final node in the chain that decrypts your data and sends it to its destination.
The Tor Network and Nodes
The Tor consists of thousands of volunteer-operated nodes circulated globally. The diversity of nodes enhances anonymity, as it’s nearly impossible for any single entity to control enough nodes to de-anonymize users effectively.
How to Access the Dark Web Safely?
There could be countless reasons anyone would want to access the dark web. They could be a journalist following a story or a human rights activist collaborating with a journalist to give voice to some story. But whatever you do, you need to keep your identity hidden. Using the Tor browser to access the dark web without any safety measures makes you vulnerable to various cyber threats and risks your digital privacy.
Achieving maximum online protection on the Tor browser is tricky, but it isn’t impossible. From now on, when you use the Tor browser, consider practicing the best security tips:
How To Use Tor Browser Safely
There could be countless reasons anyone would want to access the dark web. They could be a journalist following a story or a human rights activist collaborating with a journalist to give voice to some story. But whatever you do, you need to keep your identity hidden. Using the Tor browser to access the dark web without any safety measures makes you vulnerable to various cyber threats and risks your digital privacy.
Achieving maximum online protection on the Tor browser is tricky, but it isn’t impossible. From now, when you use the Tor browser so, consider practicing the best security tips:
1. Downloading the Tor Browser Safely
The easiest way to get started with Tor is by using the Tor Browser, a customized version of Mozilla Firefox designed for enhanced privacy and security. Here’s how to download it:
- Install Tor Tor-compatible VPN.
- Enable the VPN connection.
- Next, Visit the official Tor Project website at www.torproject.org.
- Download as per your system requirement.
2. Installing Tor on Different Platforms
Installing Tor is straightforward, but the process can vary slightly depending on your operating system. Let’s take a quick look at how to install it on Windows, macOS, and Linux.
Windows:
- Run the Tor Browser installer that you downloaded.
- Choose your language and destination folder, then click “Install.”
- launch the Tor Browser.
macOS:
- Drag the Tor Browser application into your Applications folder.
- Open the Applications folder and double-click the Tor Browser icon to launch it.
Linux:
- Extract the downloaded Tor Browser package to your preferred location.
- To the extracted folder and double-click the “start-tor-browser.desktop” file.
4. Verifying the Authenticity of the Tor Browser
It’s crucial to ensure that you’ve downloaded the legitimate Tor Browser to avoid potential security risks. The Tor Project provides instructions for verifying the authenticity of your download using digital signatures. Follow these steps to verify your Tor Browser:
- Visit the Tor Browser download page on the Tor Project website.
- Next to the download links, you’ll find a link labeled “signature.” Click it to download the signature file.
- Download the Tor Browser for your platform and save it to the same directory as the signature file.
- Open a terminal or command prompt and navigate and locate where you saved the files.
- Verify the signature using GPG (GNU Privacy Guard) with the following command (replace `tor-browser-linux64-11.0.3_en-US.tar.xz` with your actual file name):
gpg --verify tor-browser-linux64-11.0.3_en-US.tar.xz.asc tor-browser-linux64-11.0.3_en-US.tar.xz- 6. You should see a message indicating that the signature is good.
With your Tor Browser downloaded and verified, you’re ready to configure it for maximum safety.
5. Configuring Tor for Maximum Safety
The default settings of the Tor Browser are configure to provide a balance between security and usability. However, depending on your threat model and browsing habits, you may want to adjust these settings to maximize your safety and privacy. Here’s how:
Tor Browser Security Settings
Security Slider Settings
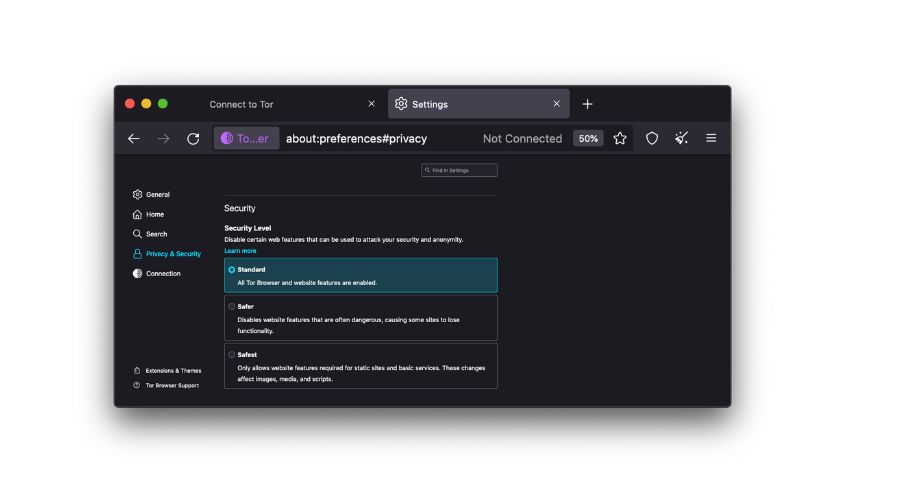
The Tor Browser includes a security slider that allows you to adjust your level of privacy and security. You can choose between four preset levels:
- Safest: Maximum security, but some websites may not function correctly.
- Safer: A good balance between security and usability.
- Standard: Default settings for most users.
- Lowest: Minimal security, similar to a regular web browser.
To access the security slider:
- Open the Tor Browser.
- Click the Tor icon (green onion) in the top-left corner.
- Choose “Security Settings.”
- Slide the security level to your desired setting.
Privacy Preferences
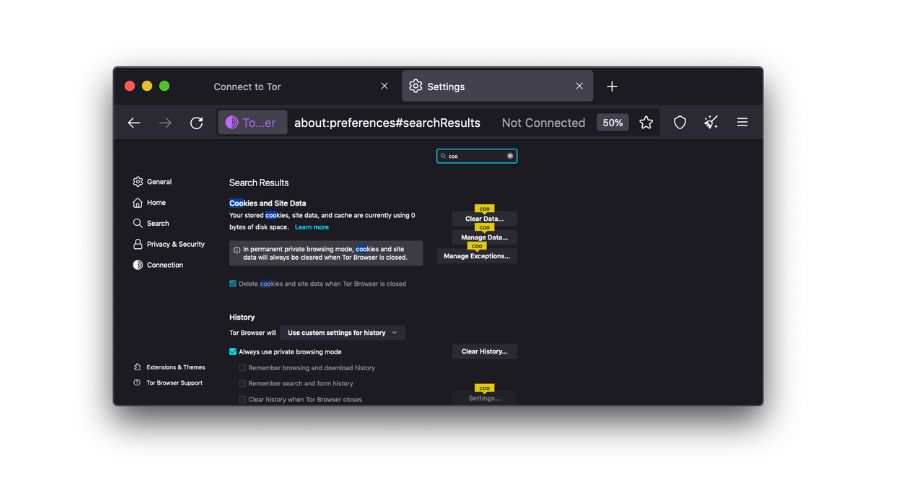
In the Tor Browser, you can fine-tune privacy settings by clicking on the “Privacy & Security” option in the menu. Here, you can:
- Block all third-party cookies: Prevent websites from tracking you using cookies.
- Block all canvas fingerprinting: Protect against canvas fingerprinting, a technique used to identify users.
- Block all WebRTC IP handling: Prevent WebRTC leaks that could reveal your real IP address.
These settings can help you further enhance your privacy while using Tor.
Stay tuned for the next section, where we’ll delve into protecting your identity while using Tor.
6. Protecting Your Identity
Using Tor effectively also means safeguarding your identity and personal information. While Tor provides strong anonymity, following best practices to minimize the risk of accidentally revealing your identity online is essential.
Anonymous Browsing Practices
- Avoid Logging In: Refrain from logging into personal accounts while using Tor. Logging in can link your online activity to your real identity.
- Use Disposable Email Addresses: When registering on websites or services while on Tor, consider using temporary or disposable email addresses to maintain anonymity.
Avoiding Browser Fingerprinting
Websites and trackers often use browser fingerprinting to identify users based on their unique browser configurations. To counter this:
- Use the Tor Browser: The Tor Browser is designed to minimize fingerprinting by providing a uniform configuration for all users.
Managing Cookies and Tracking
- Block Third-Party Cookies: Configure your Tor Browser to block all third-party cookies. This prevents advertisers and trackers from following your activity across websites.
- Regularly Clear Cookies and Data: Periodically clear your browser’s cookies and browsing data to minimize tracking.
IP Address Leakage Prevention
Tor is effective at hiding your IP address, but some leaks can still occur. To prevent IP address leakage:
- Regularly Check for IP Leaks: Use online tools like “https://check.torproject.org/” to ensure your IP address is properly concealed.
- Avoid Torrenting and P2P: Torrenting or using peer-to-peer (P2P) services on Tor is not recommended, as it can reveal your IP address.
Adhering to these practices can significantly enhance your anonymity while using the Tor network.
7. Safe Searching and Surfing
Even when using Tor, it’s essential to maintain safe browsing habits to protect yourself from potential threats and maintain your privacy.
Using Search Engines on Tor
- Use Privacy-Focused Search Engines: Opt for search engines like DuckDuckGo or Startpage, which don’t track your searches or collect personal information.
- Access .onion Sites: Some search engines, like DuckDuckGo, offer the option to search for .onion websites within the Tor network.
Safe Browsing Habits
- Check Website URLs: Always double-check the URLs of websites you visit to ensure you’re on the correct, secure site.
- Avoid Downloading Suspicious Content: Refrain from downloading files or software from untrusted sources, as they may contain malware.
- Use HTTPS: Ensure that the websites you visit use HTTPS encryption for secure connections.
- Don’t Enable Scripts Unnecessarily: In the Tor Browser, NoScript can block potentially harmful scripts on websites. Only allow scripts on trusted sites.
- Stay updaated: Keep yourself updated on the latest threats and vulnerabilities that may affect Tor users.
By practicing safe searching and surfing, you reduce the risk of encountering harmful content or compromising your anonymity on the Tor network.
In the next section, we’ll explore encrypting communications while using Tor, including sending secure emails and using instant messaging services.
8. Encrypting Communications
One of the essential aspects of maintaining privacy and security while using Tor is ensuring that your communications are adequately encrypted. Here, we’ll explore how to send secure emails and use instant messaging services over the Tor network.
Sending Secure Emails with Tor
Emails can contain sensitive information, and ensuring their security is paramount. To send secure emails over Tor:
- Use Encrypted Email Services: Consider email services offering end-to-end encryption, such as ProtonMail or Tutanota. These services provide an added layer of security for your communications.
- Enable Tor Birdy (Thunderbird): If you use the Thunderbird email client, you can install the Tor Birdy add-on to route your emails through the Tor network.
- PGP Encryption: Implement Pretty Good Privacy (PGP) encryption for your emails to ensure that even if intercepted, they remain confidential.
Using Tor for Instant Messaging
Instant messaging applications are another common means of communication. To secure your instant messaging over Tor:
- Use Tor-Compatible Messaging Apps: Look for messaging apps that are designed to work with Tor, such as Tor Messenger or Ricochet.
- Use Off-the-Record (OTR) Encryption: OTR encryption ensures that your chat conversations are private and secure.
- Avoid Sharing Personal Information: Be cautious about sharing personal information over instant messaging, even when using Tor. Information leaks can occur if not handled carefully.
- Check Server Locations: Some messaging services may route your messages through exit nodes in different countries, potentially exposing your communications. Verify the service’s security features.
By following these practices, you can maintain the confidentiality and security of your communications while using Tor.
9. Staying Safe on Tor Forums and Communities
Tor has a vibrant online community of users and supporters. Participating in discussions, sharing experiences, and seeking assistance are integral to the Tor experience. However, it’s essential to stay safe while engaging with these communities:
Best Practices for Tor-Related Discussions
- Use Pseudonyms: Avoid using your real name or personal information in forum profiles or discussions. Use pseudonyms to protect your identity.
- Avoid Sharing Sensitive Information: Be cautious about sharing personal details or information that could be used to identify you.
- Stay Informed: Familiarize yourself with the specific forum or community rules and guidelines to avoid inadvertently breaking any laws.
Avoiding Scams and Phishing Attempts
- Be Skeptical: Exercise caution when encountering offers that seem too good to be true or requests for personal information.
- Verify Links: Before clicking on any links or downloading files shared on forums, ensure they are from trusted sources.
- Report Suspicious Activity: If you encounter suspicious or malicious activity, report it to the forum administrators or moderators.
Staying safe in Tor communities involves a combination of vigilance and adherence to best practices. It’s a valuable resource for support and information when used wisely.
In the next section, we’ll delve into using Tor on mobile devices and explore the specific considerations and applications available for Android and iOS.
10. Tor on Mobile Devices
Extending your use of Tor to mobile devices is crucial for maintaining your privacy on the go. Below, we’ll explore how to install Tor on Android and iOS, along with essential security considerations.
Installing Tor on Android
- Download Orbot: Orbot is the official Tor proxy app for Android. You can find it on the Google Play Store. Install and open it.
- Configure Orbot: Follow the setup wizard to configure Orbot. You can choose to use Tor for all apps or specific ones. Make sure to enable the VPN mode for maximum privacy.
- Install Orfox (Optional): For secure browsing on Android, consider using Orfox, which is a Tor Browser-based app designed for mobile devices. You can find it on the Google Play Store.
Installing Tor on iOS
As of my last knowledge update in September 2021, there was no official Tor Browser for iOS due to Apple’s restrictions. However, you can use third-party Tor-enabled apps like Onion Browser on the App Store. Be cautious when selecting third-party apps, ensuring they have a reputable privacy and security history.
Mobile Security Considerations
When using Tor on mobile devices, keep the following in mind:
- App Permissions: Review app permissions carefully. Avoid apps that request unnecessary access to your device’s data or features.
- Update Regularly: Keep your mobile operating system and Tor-related apps up to date to patch security vulnerabilities.
- Secure Your Device: Use strong, unique passcodes or biometric authentication to protect your device.
- Limit Public Wi-Fi Use: Be cautious when connecting to public Wi-Fi networks. Consider using a VPN in addition to Tor for extra security.
- Avoid Jailbreaking or Rooting: Modifying your device’s operating system can weaken security. Stick to official app stores and avoid jailbreaking (iOS) or rooting (Android) your device.
With Tor installed on your mobile device and these security considerations in mind, you can maintain your privacy while on the move.
Additional Tips and Tricks
Beyond the fundamental steps for using Tor safely, there are additional tips and tricks to enhance your online security and anonymity:
Regularly Updating Tor Browser
Ensure your Tor Browser is always up to date to receive the latest security fixes and improvements.
Creating Strong and Unique Passwords
Use a reputable password manager to generate and store strong, unique passwords for your accounts.
Using a VPN with Tor
While Tor provides anonymity within the network, using a VPN in conjunction with Tor can add an extra layer of security by hiding your Tor usage from your ISP.
Enabling Two-Factor Authentication
Whenever possible, enable two-factor authentication (2FA) on your online accounts for an added layer of security.
Keeping Software and OS Up to Date
Regularly update your operating system, software, and security tools to patch vulnerabilities.
In the next section, we’ll address common issues users may encounter while using Tor and how to troubleshoot them.
Troubleshooting Common Issues
Using Tor can be a smooth experience, but occasional issues may arise. Here are solutions to some common problems users encounter:
Slow Tor Browsing
- Choose a Different Entry Node: If you’re experiencing slow speeds, Tor may be routing your traffic through a congested or slow entry node. Try disconnecting and reconnecting to get a different entry node.
- Adjust Security Slider: Lowering the security slider to a lower setting can speed up your browsing experience, but be cautious as this might compromise your anonymity.
Websites Blocking Tor
- Use Bridges: If websites are blocking Tor exit nodes, you can configure your Tor Browser to use bridges (obfuscated servers) to access the network.
- Check Tor Exit Policies: Some websites might block known Tor exit nodes. In such cases, there’s little you can do except contacting the website administrator.
Dealing with CAPTCHA Challenges
- Enable JavaScript Temporarily: Some websites use JavaScript-based CAPTCHAs that won’t work with JavaScript disabled. You can temporarily enable JavaScript in your Tor Browser to solve these CAPTCHAs but remember to disable it afterward.
- Use Onion Services: Whenever possible, use websites that offer .onion versions of their services. These sites are often more Tor-friendly.
Connection Problems
- Check Network Connection: Ensure you have a stable internet connection before using Tor.
- Reset Tor Browser: If you encounter persistent connection issues, try resetting your Tor Browser settings to default and configuring them again.
Remember that while Tor aims to provide anonymity and security, it’s not immune to all issues. Some websites may not work correctly due to the anonymity measures in place, so be prepared to compromise between security and usability when necessary.
Conclusion
In this comprehensive guide, we’ve covered everything you need to know about using Tor safely and effectively. From setting up Tor and configuring it for maximum safety to protecting your identity, encrypting communications, and troubleshooting common issues, you can confidently navigate the Tor network.
Online privacy and security are more critical than ever, and Tor is a powerful tool to help you maintain your anonymity. However, remember to use Tor responsibly and ethically, respecting the laws and regulations of your jurisdiction.
By following the steps and best practices outlined in this guide, you can enjoy the benefits of the Tor network while safeguarding your privacy and security in an increasingly interconnected digital world.
